Strong cyber security is no longer optional. It is a critical business operation that protects your safety, profitability, and future plans. But you can’t mount an effective defence if you don’t understand your biggest risk factors. This is precisely why every good security strategy starts with an audit.
But what is a cyber security audit? And how can you perform one?
What is a Cyber Security Audit?
A cyber security audit is a comprehensive assessment that helps you identify security issues within your business. It forms the basis of your overall defense plan, providing the information you need to effectively protect sensitive data and prevent breaches. It is also extremely important for compliance and thus, client trust. Regular audits prove that you take security seriously, which brings you into alignment with regulations and builds strong relationships.
If you are trying to improve your security posture, step one should always be a security audit. Here’s how you can perform one.
Step 1: Define the Scope of the Audit
Before anything else, you must define the cyber security audit’s scope. Perform a thorough IT assessment that catalogues all:
- Hardware
- Software
- Network Infrastructure
- Cloud services
- Mobile devices and remote access systems
- Users, policies, and access controls
This step tells you what you’re working with, and helps avoid wasted time later in the process.
Step 2: Assess Your Security Posture
Now that you understand your IT infrastructure, it’s time to see how well-defended it is. Perform an analysis of every risk factor your business experiences. Which cyber-attacks are you likely to face? Are insider threats a concern? Prioritise these by the amount of damage each one could cause your business. A traffic light system may be useful, here:
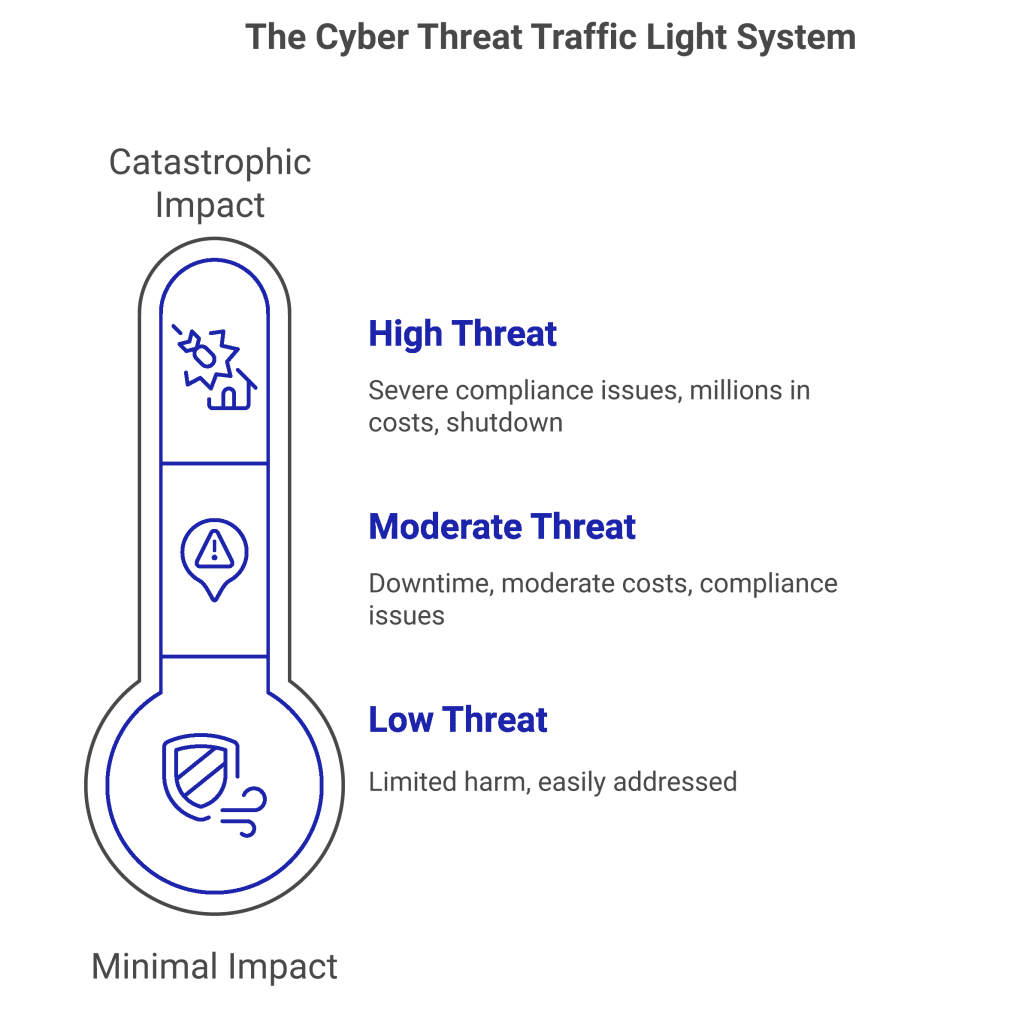
Next, create a list of your current security measures and compare them against your prioritised cyber threats. This will allow you to detect gaps that need to be addressed.
Step 3: Review Compliance
As data protection laws tighten and penalties rise, compliance has become an increasingly important consideration. During your cyber security audit, review the regulations your business is subject to and check that you are fully compliant. If you are not, note down any gaps that you find.
Step 4: Analyse Findings
With the information you have gathered, you will now create a game plan. Analyse your findings and identify some strategies that can help close any gaps you discovered. Start with the most dangerous “Red light” threats first, along with compliance issues. These must be addressed immediately. Then, any leftover resources can be used to combat yellow and green threats.
Create a report with your findings, and present it to key stakeholders. Outline the importance of these measures, explain which resources will be necessary, and assign clear responsibilities. Early buy-in will be crucial for the success of your follow-up measures.
Step 5: Enact Your Improvement Plan
Once the audit is complete, begin implementing your improvement plan. Work in stages to avoid draining your resources too quickly, starting with the most concerning issues first. Aim for high-impact, low-cost fixes where possible – for example, multi-factor authentication or stronger access controls.
If you have an external security team, now is a good time to put them to work. They can help you address these vulnerabilities swiftly and effectively, while providing guidance on further steps you can take.
Remember to document each action taken in your audit report. This written evidence could be useful for demonstrating compliance, if necessary.
FAQs
Do I Need a Cyber Security Audit Template?
In the interest of staying organised, some businesses use a cyber security audit template. These can be found online, and may make it practices to identify security weaknesses and ensure compliance with legal and industry standards.
How Much Does a Cyber Security Audit Cost?
The cost of cyber security audits in Australia varies depending on the type of audit (whether you carry it out yourself or hire a professional), the size of your business, and the complexity of your IT infrastructure.
Should I Use Cyber Security Audit Tools?
While cyber security audit tools do exist, they are largely unnecessary. If you need help it is almost always better to download a template or partner with a managed service provider.
Are There Different Types of Cyber Security Audits in Australia?
The two main types of cyber security audits are an internal audit (performed by you) and an external audit (performed by a third-party expert). You may choose whichever path best suits your business.
Can a Managed Service Provider Perform a Small Business Cyber Security Audit For Me?
Yes. If you don’t feel equipped to perform an audit on your own, some managed service providers can do it for you. If you’re uncertain, feel free to ask your provider for more information.
Discover How to Secure Your Business
A well-executed cyber audit ensures that your business is prepared to face any threat. It might seem complicated at first, but it really doesn’t need to be. With the right guidance and preparation, you can reduce the risk of data breaches and cyber incidents, setting your company up for long-term success.
National IT is here to help you protect your business. Our expert insights will give you all the information you need for a brighter, safer future. Get started with the ultimate guide to cyber security today.

